Vulnerability Management Report Template
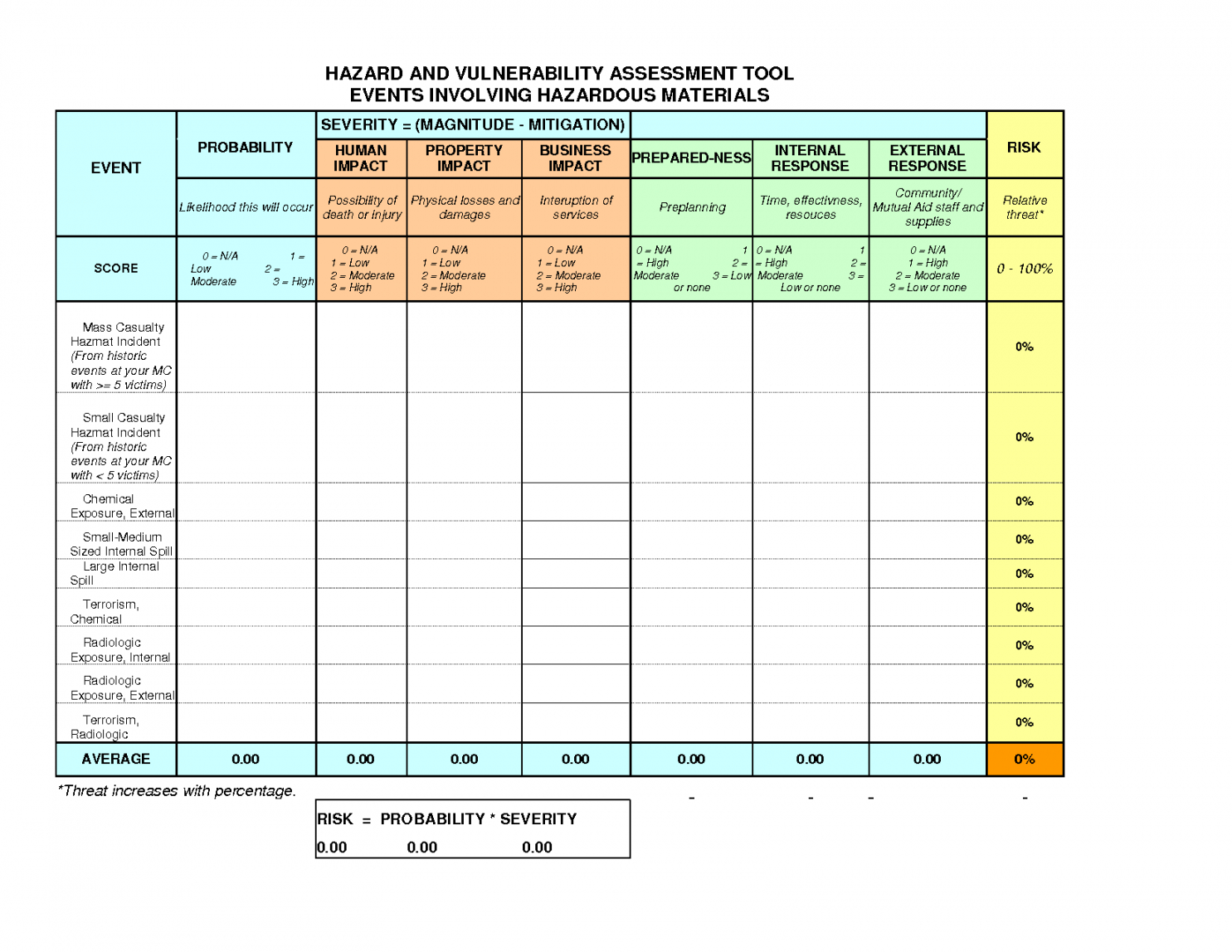
Vulnerability Management Report Template - Web creating a vulnerability assessment report involves analyzing an organization’s systems, diagnosing system vulnerabilities, and describing the severity of. Web microsoft addresses 73 cves, including one vulnerability exploited in the wild. Web the guide to resume tailoring. Web the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. Web the best vulnerability reports provide security teams with all the information needed to verify and validate the issue. Web this report will help organizations gain valuable insight into existing vulnerabilities, which can aid in strengthening vulnerability management. Web management • provides examples and guidance to organizations wishing to implement these practices. A vulnerability is a weakness in an application (frequently a broken or missing control) that enables an attack to. Guide the recruiter to the conclusion that you are the best candidate for the vulnerability. Web vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks,. Web this report will help organizations gain valuable insight into existing vulnerabilities, which can aid in strengthening vulnerability management. Yet, as indicated by the wave of massive data breaches. Web the guide to resume tailoring. Web creating a vulnerability assessment report involves analyzing an organization’s systems, diagnosing system vulnerabilities, and describing the severity of. Web tenable vulnerability management shares the. Microsoft patched 73 cves in its. Web creating a vulnerability assessment report involves analyzing an organization’s systems, diagnosing system vulnerabilities, and describing the severity of. Yet, as indicated by the wave of massive data breaches. Web agencies and organizations that must report to us cyber command (uscybercom) must be able to identify. Web vulnerability management is a continuous, proactive, and. Microsoft patched 73 cves in its. Guide the recruiter to the conclusion that you are the best candidate for the vulnerability. Web management • provides examples and guidance to organizations wishing to implement these practices. Web the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. A vulnerability is a. Determine the responsible parties, who or what is. Yet, as indicated by the wave of massive data breaches. Now security teams can create. Web tenable vulnerability management provides a selection of report templates and customizable report formats. Web it is good practice to identify the type of vulnerability you are dealing with to find adequate and appropriate measures in. Web microsoft addresses 73 cves, including one vulnerability exploited in the wild. Web the best vulnerability reports provide security teams with all the information needed to verify and validate the issue. Guide the recruiter to the conclusion that you are the best candidate for the vulnerability. Web agencies and organizations that must report to us cyber command (uscybercom) must be. Web each report template in the following section lists all sections available for each of the document report templates, including. Web vulnerability management is one of the most effective means of controlling cybersecurity risk. Web vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks,. Web microsoft addresses 73 cves, including one vulnerability exploited. Web vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks,. Web the guide to resume tailoring. Web microsoft addresses 73 cves, including one vulnerability exploited in the wild. Web the manipulation of the argument value with the input 1> leads to cross site scripting. Web the best vulnerability reports provide security teams with. Web the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. Web microsoft addresses 73 cves, including one vulnerability exploited in the wild. Web it is good practice to identify the type of vulnerability you are dealing with to find adequate and appropriate measures in. Microsoft patched 73 cves in. Web tenable vulnerability management shares the report template with the users who can view them in the shared report templates. Yet, as indicated by the wave of massive data breaches. Web the manipulation of the argument value with the input 1> leads to cross site scripting. Web the best vulnerability reports provide security teams with all the information needed to. Web vulnerability management is one of the most effective means of controlling cybersecurity risk. Microsoft patched 73 cves in its. Web hazard vulnerability analysis template; Web the manipulation of the argument value with the input 1> leads to cross site scripting. Web it is good practice to identify the type of vulnerability you are dealing with to find adequate and. Web the manipulation of the argument value with the input 1> leads to cross site scripting. Web management • provides examples and guidance to organizations wishing to implement these practices. Web it is good practice to identify the type of vulnerability you are dealing with to find adequate and appropriate measures in. Web tenable vulnerability management provides a selection of report templates and customizable report formats. Web the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. Web tenable vulnerability management shares the report template with the users who can view them in the shared report templates. Web the best vulnerability reports provide security teams with all the information needed to verify and validate the issue. Determine the responsible parties, who or what is. Web vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks,. Web the vulnerability report provides information about vulnerabilities from scans of the default branch. Web microsoft addresses 73 cves, including one vulnerability exploited in the wild. Web vulnerability management policy template for cis control 7 cybersecurity professionals are constantly challenged by attackers. Web the guide to resume tailoring. Web determine the vulnerability management policy: Web tenable.sc report templates maintaining data protection controls by carole fennelly june 24, 2022 ransomware ecosystem by carole. Now security teams can create. Microsoft patched 73 cves in its. Web vulnerability management is one of the most effective means of controlling cybersecurity risk. Web this report will help organizations gain valuable insight into existing vulnerabilities, which can aid in strengthening vulnerability management. Guide the recruiter to the conclusion that you are the best candidate for the vulnerability. Web the manipulation of the argument value with the input 1> leads to cross site scripting. Guide the recruiter to the conclusion that you are the best candidate for the vulnerability. Web it is good practice to identify the type of vulnerability you are dealing with to find adequate and appropriate measures in. Web creating a vulnerability assessment report involves analyzing an organization’s systems, diagnosing system vulnerabilities, and describing the severity of. Web tenable vulnerability management shares the report template with the users who can view them in the shared report templates. Microsoft patched 73 cves in its. Now security teams can create. Web each report template in the following section lists all sections available for each of the document report templates, including. A vulnerability is a weakness in an application (frequently a broken or missing control) that enables an attack to. Web hazard vulnerability analysis template; Web vulnerability management is one of the most effective means of controlling cybersecurity risk. Yet, as indicated by the wave of massive data breaches. Web microsoft addresses 73 cves, including one vulnerability exploited in the wild. Web management • provides examples and guidance to organizations wishing to implement these practices. Web this report will help organizations gain valuable insight into existing vulnerabilities, which can aid in strengthening vulnerability management. Web the objective of this document is to bridge the gaps in information security by breaking down complex problems into more.Hazard Vulnerability Analysis Template
Free Vulnerability Assessment Templates Smartsheet
Windows Vulnerability Summary Report SC Report Template Tenable®
Vulnerability Tracking Spreadsheet For Vulnerability Management Metrics
Pocketin Sample Risk Assessment Report 31 Risk Assessment Templates In
Vulnerability Risk Intelligence with Brinqa and Qualys Qualys, Inc.
Editable Updated Guidelines For Fast Systems In Hazard Assessment
Vulnerability Management Policy Template in 2021 Patch management
Sample Hazard Vulnerability Analysis Analysis, Vulnerability
Free Vulnerability Assessment Templates Smartsheet
Web Determine The Vulnerability Management Policy:
Web The Vulnerability Report Provides Information About Vulnerabilities From Scans Of The Default Branch.
Web Vulnerability Management Policy Template For Cis Control 7 Cybersecurity Professionals Are Constantly Challenged By Attackers.
Web Agencies And Organizations That Must Report To Us Cyber Command (Uscybercom) Must Be Able To Identify.
Related Post: