Network Security Checklist Template
Network Security Checklist Template - Ultimate network security checklist 3. A network security audit checklist is utilized to proactively assess the guarantee and. Web download free template. Web use this risk assessment template specifically designed for it and network security. This checklist does not provide vendor specific security considerations but rather. Is the network device considered a core network. Use this risk assessment template specifically designed for it and. Web pdf template, a network security audit checklist is used to proactively assess the security and integrity of organizational. Education network security checklist 2. Web a thorough policy will cover topics such as: Perform a penetration test 8. Review how network access happens 7. Web network security audit checklist. Web malware, denial of service attacks, and remote control access are just a few of the various threats networks face. Web free 5+ network security checklist templates in pdf 1. Web titanhq can provide you with a template for creating your own network security checklist and hardening your network against. Review how network access happens 7. A network security audit checklist is utilized to proactively assess the guarantee and. Web pdf template, a network security audit checklist is used to proactively assess the security and integrity of organizational. General a. Scores 4.81 with 384 votes. This checklist does not provide vendor specific security considerations but rather. A network security audit checklist is utilized to proactively assess the guarantee and. Review how network access happens 7. Verify the existing network security policy 3. The network device is secured in an area with physical access control. Target what’s not working well 6. Web proactively maintain net security by conducting network security assessments using customizable network. Web titanhq can provide you with a template for creating your own network security checklist and hardening your network against. Web download free template. Settle on the audit’s scope 4. Verify the existing network security policy 3. Web use this risk assessment template specifically designed for it and network security. Target what’s not working well 6. Review how network access happens 7. Review how network access happens 7. Web introduction this checklist should be used to audit a firewall. Web this article contains information about what a network security checklist is, as well as steps on improving your network security. Web network security checklist. Use this risk assessment template specifically designed for it and. Web this article contains information about what a network security checklist is, as well as steps on improving your network security. Web download free template. Web process street network security audit checklist is engineered to be used to assist a risk manager or equivalent it professional. Perform a penetration test 8. Web network security audit checklist. Settle on the audit’s scope 4. Web a thorough policy will cover topics such as: Scores 4.81 with 384 votes. Web titanhq can provide you with a template for creating your own network security checklist and hardening your network against. Web network security risk assessment template. The network device is secured in an area with physical access control. Web download this free security audit checklist to verify the effectiveness of your organization’s security measures and. Settle on the audit’s scope 4. Perform a penetration test 8. • acceptable use policy, to specify what types of network. Web network security risk assessment template. Web malware, denial of service attacks, and remote control access are just a few of the various threats networks face. Settle on the audit’s scope 4. Perform a penetration test 8. Education network security checklist 2. Education network security checklist 2. Web network security risk assessment template. Scores 4.81 with 384 votes. The network device is secured in an area with physical access control. Verify the existing network security policy 3. Web november 1, 2019 by hari subedi in this post, we share with you a network security checklist of action items. Web process street network security audit checklist is engineered to be used to assist a risk manager or equivalent it professional. Decide on the necessary tools or personnel 2. Web this article contains information about what a network security checklist is, as well as steps on improving your network security. Web network security checklist. Web network security audit checklist. Use this risk assessment template specifically designed for it and. Web 6 steps to secure your network now that you understand the basics of network security, review these six steps to create a holistic. Web download free template. Settle on the audit’s scope 4. Review how network access happens 7. This checklist does not provide vendor specific security considerations but rather. Ultimate network security checklist 3. Web malware, denial of service attacks, and remote control access are just a few of the various threats networks face. Is the network device considered a core network. Web 6 steps to secure your network now that you understand the basics of network security, review these six steps to create a holistic. Settle on the audit’s scope 4. Understand which threats to look for 5. Verify the existing network security policy 3. Web proactively maintain net security by conducting network security assessments using customizable network. Web a thorough policy will cover topics such as: Web this article contains information about what a network security checklist is, as well as steps on improving your network security. Use this risk assessment template specifically designed for it and. General a written network security policy that lists the rights and responsibilities of all staff, employees, and consultants security. Review how network access happens 7. Web titanhq can provide you with a template for creating your own network security checklist and hardening your network against. Web introduction this checklist should be used to audit a firewall. The network device is secured in an area with physical access control. Decide on the necessary tools or personnel 2. Web free 5+ network security checklist templates in pdf 1. Web malware, denial of service attacks, and remote control access are just a few of the various threats networks face.Small Firm Cybersecurity Checklist
10 Network assessment Checklist Template SampleTemplatess
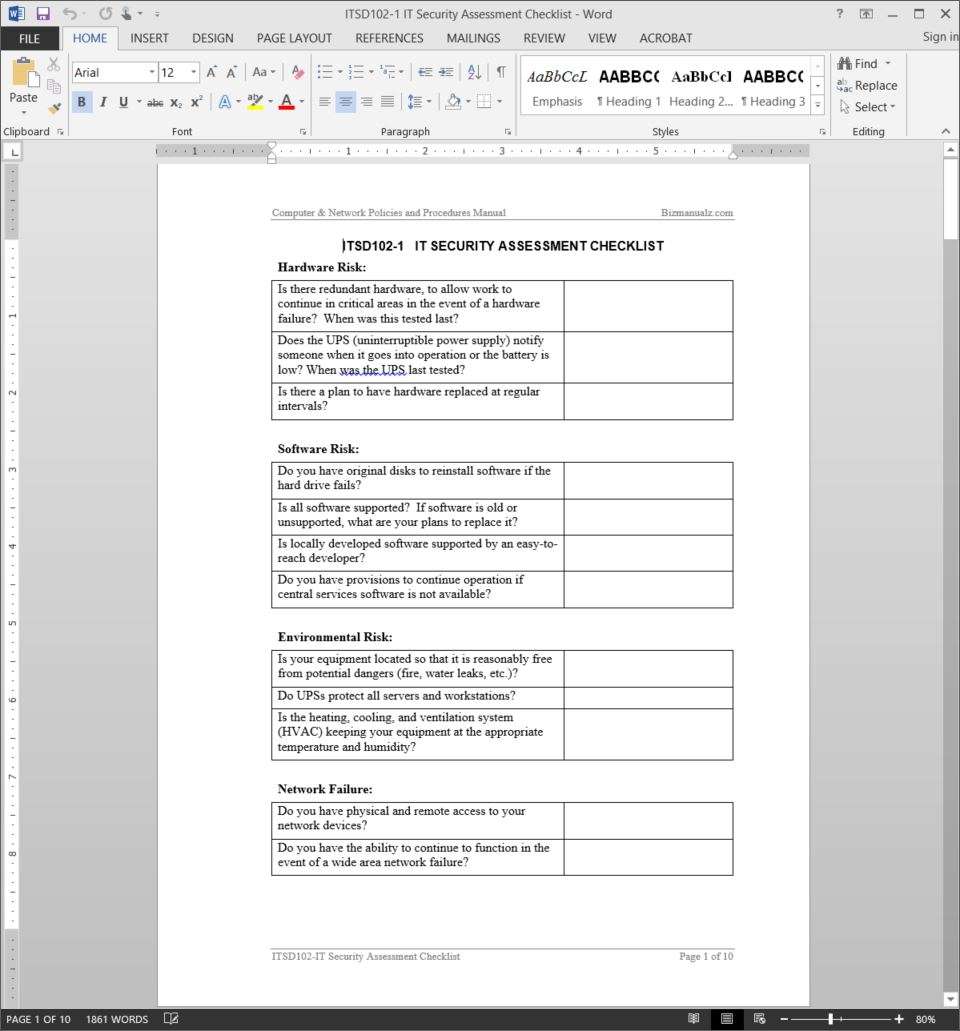
IT Security Assessment Checklist Template
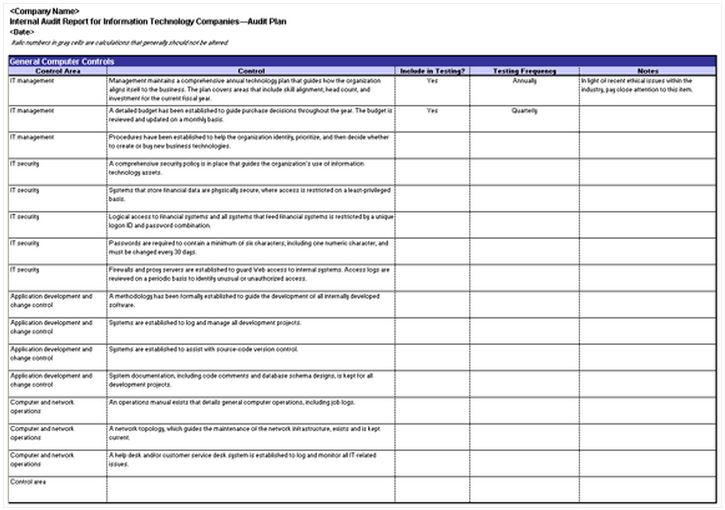
Security Audit Network Security Audit Checklist Pdf
Network Infrastructure assessment Template Inspirational Security Guard
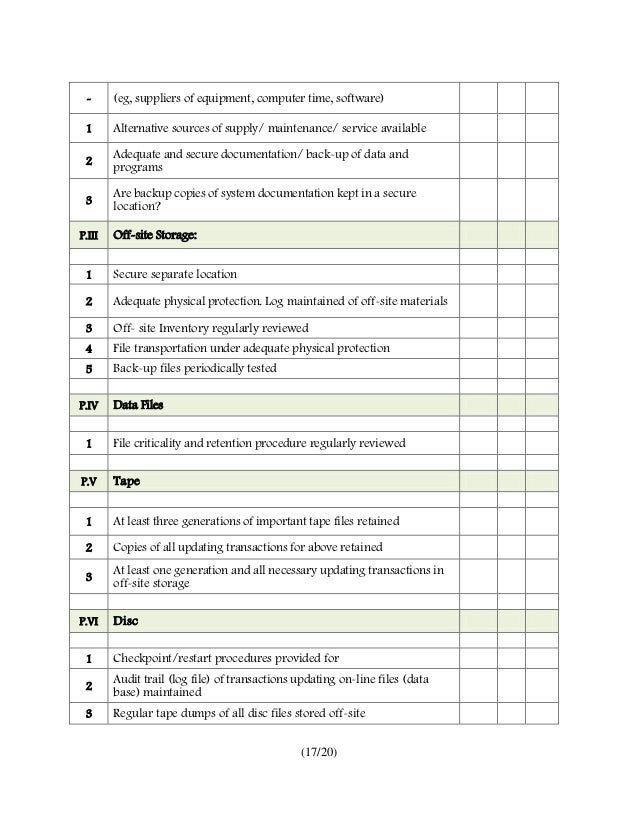
Security Audit Network Security Audit Checklist Pdf
Get Our Image of Security Assessment Checklist Template for Free
Physical Security Checklist Template Fresh 27 Of Network Security
It Security Audit Checklist Template Best Of 26 Of Facility Security
√ Free Printable IT Security Checklist Template Checklist Templates
• Acceptable Use Policy, To Specify What Types Of Network.
Web November 1, 2019 By Hari Subedi In This Post, We Share With You A Network Security Checklist Of Action Items.
Education Network Security Checklist 2.
Web Network Security Risk Assessment Template.
Related Post: