Vulnerability Report Template
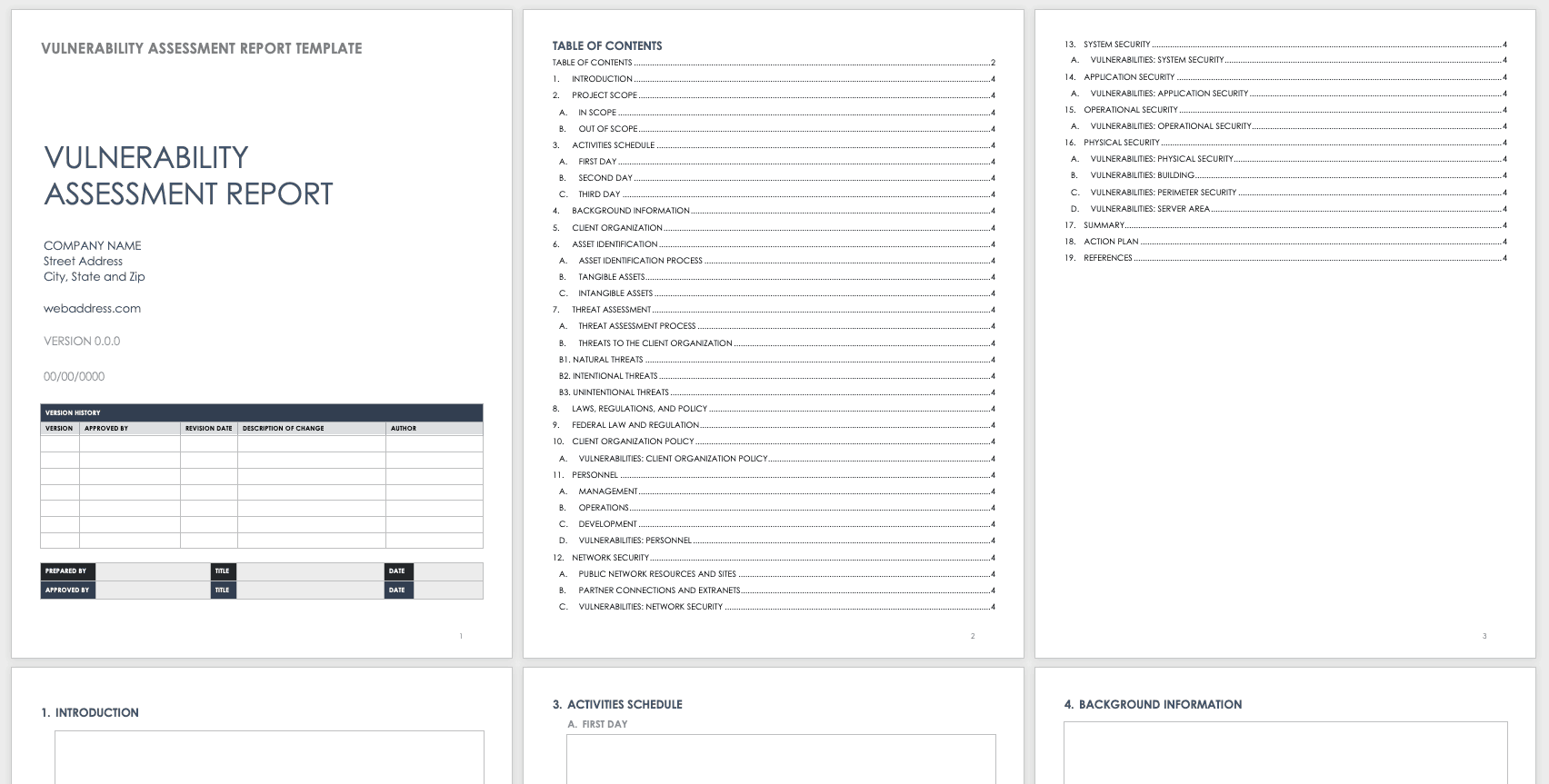
Vulnerability Report Template - The report is available in the. Web ultimate the vulnerability report provides information about vulnerabilities from scans of the default branch. Web typically, a vulnerability assessment report will show you the raw number of vulnerabilities detected in your systems at. So, hop on over to. What is the problem that creates the vulnerability? It contains a detailed analysis of the. Web the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. Web step 1 of writing a good report: Web a vulnerability report is a document provided by security testers after the assessment of a target’s security. Web this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. Web ultimate the vulnerability report provides information about vulnerabilities from scans of the default branch. The report is available in the. Web assessing a vulnerability and reporting on it can assist to reduce the danger it poses to individuals and society. It contains a detailed analysis of the. Web the manipulation of the argument value with the input 1> leads. Now security teams can create. Written by experienced security experts. Web the manipulation of the argument value with the input 1> leads to cross site scripting. Web last week, there were 64 vulnerabilities disclosed in 66 wordpress plugins and 3 wordpress themes that. Web the best vulnerability reports provide security teams with all the information needed to verify and validate. The following feature is not supported in tenable vulnerability management federal risk and. Web ultimate the vulnerability report provides information about vulnerabilities from scans of the default branch. Web please use this template to report a vulnerability in pi communication protocols. In case you would like to report a. Web the manipulation of the argument value with the input 1>. Web typically, a vulnerability assessment report will show you the raw number of vulnerabilities detected in your systems at. Web wordfence intelligence weekly wordpress vulnerability report (july 31, 2023 to august 6, 2023) last week, there were. In case you would like to report a. Web download our free vulnerability assessment template today! 9 min cobalt the pentest process is. In case you would like to report a. Web please use this template to report a vulnerability in pi communication protocols. Web assessing a vulnerability and reporting on it can assist to reduce the danger it poses to individuals and society. Written by experienced security experts. Web ultimate the vulnerability report provides information about vulnerabilities from scans of the default. The report is available in the. Web wordfence intelligence weekly wordpress vulnerability report (july 31, 2023 to august 6, 2023) last week, there were. 9 min cobalt the pentest process is not limited to executing various test cases to. So, hop on over to. What is the problem that creates the vulnerability? Web assessing a vulnerability and reporting on it can assist to reduce the danger it poses to individuals and society. Web ultimate the vulnerability report provides information about vulnerabilities from scans of the default branch. The report is available in the. Web the manipulation of the argument value with the input 1> leads to cross site scripting. Now security teams. Web ultimate the vulnerability report provides information about vulnerabilities from scans of the default branch. In case you would like to report a. So, hop on over to. Web typically, a vulnerability assessment report will show you the raw number of vulnerabilities detected in your systems at. Craft a descriptive title and summary the first parts of a great. Web download our free vulnerability assessment template today! Written by experienced security experts. Craft a descriptive title and summary the first parts of a great. Web may 17, 2021 est read time: Web last week, there were 64 vulnerabilities disclosed in 66 wordpress plugins and 3 wordpress themes that. 9 min cobalt the pentest process is not limited to executing various test cases to. Web wordfence intelligence weekly wordpress vulnerability report (july 31, 2023 to august 6, 2023) last week, there were. So, hop on over to. Web the manipulation of the argument value with the input 1> leads to cross site scripting. Web the objective of this document. Written by experienced security experts. So, hop on over to. Web a vulnerability report is a document provided by security testers after the assessment of a target’s security. What is the problem that creates the vulnerability? In case you would like to report a. Web wordfence intelligence weekly wordpress vulnerability report (july 31, 2023 to august 6, 2023) last week, there were. Web last week, there were 64 vulnerabilities disclosed in 66 wordpress plugins and 3 wordpress themes that. Web ultimate the vulnerability report provides information about vulnerabilities from scans of the default branch. Web typically, a vulnerability assessment report will show you the raw number of vulnerabilities detected in your systems at. Web assessing a vulnerability and reporting on it can assist to reduce the danger it poses to individuals and society. The report is available in the. Web the manipulation of the argument value with the input 1> leads to cross site scripting. Now security teams can create. Web it is good practice to identify the type of vulnerability you are dealing with to find adequate and appropriate measures in. Web step 1 of writing a good report: Web the best vulnerability reports provide security teams with all the information needed to verify and validate the issue. It contains a detailed analysis of the. Web creating a vulnerability assessment report involves analyzing an organization’s systems, diagnosing system vulnerabilities, and describing the severity of. Web the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. Web may 17, 2021 est read time: Web assessing a vulnerability and reporting on it can assist to reduce the danger it poses to individuals and society. Written by experienced security experts. Now security teams can create. Web the best vulnerability reports provide security teams with all the information needed to verify and validate the issue. It contains a detailed analysis of the. Web ultimate the vulnerability report provides information about vulnerabilities from scans of the default branch. Web the manipulation of the argument value with the input 1> leads to cross site scripting. 9 min cobalt the pentest process is not limited to executing various test cases to. So, hop on over to. Craft a descriptive title and summary the first parts of a great. Web the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. Web a vulnerability report is a document provided by security testers after the assessment of a target’s security. Web download our free vulnerability assessment template today! Web creating a vulnerability assessment report involves analyzing an organization’s systems, diagnosing system vulnerabilities, and describing the severity of. The following feature is not supported in tenable vulnerability management federal risk and. Web please use this template to report a vulnerability in pi communication protocols.Free Sample Vulnerability Assessment Report PurpleSec
Free Vulnerability Assessment Templates Smartsheet
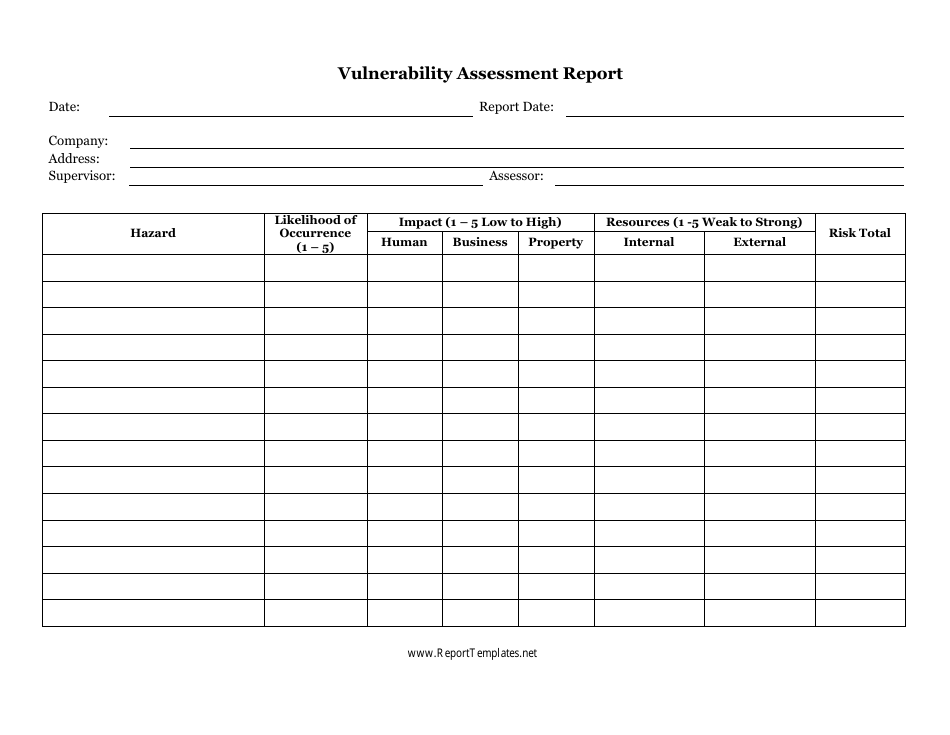
Vulnerability Assessment Report Template Download Printable PDF
28+ [ Vulnerability Report Template ] Vulnerability With Regard To
Free Vulnerability Assessment Templates Smartsheet
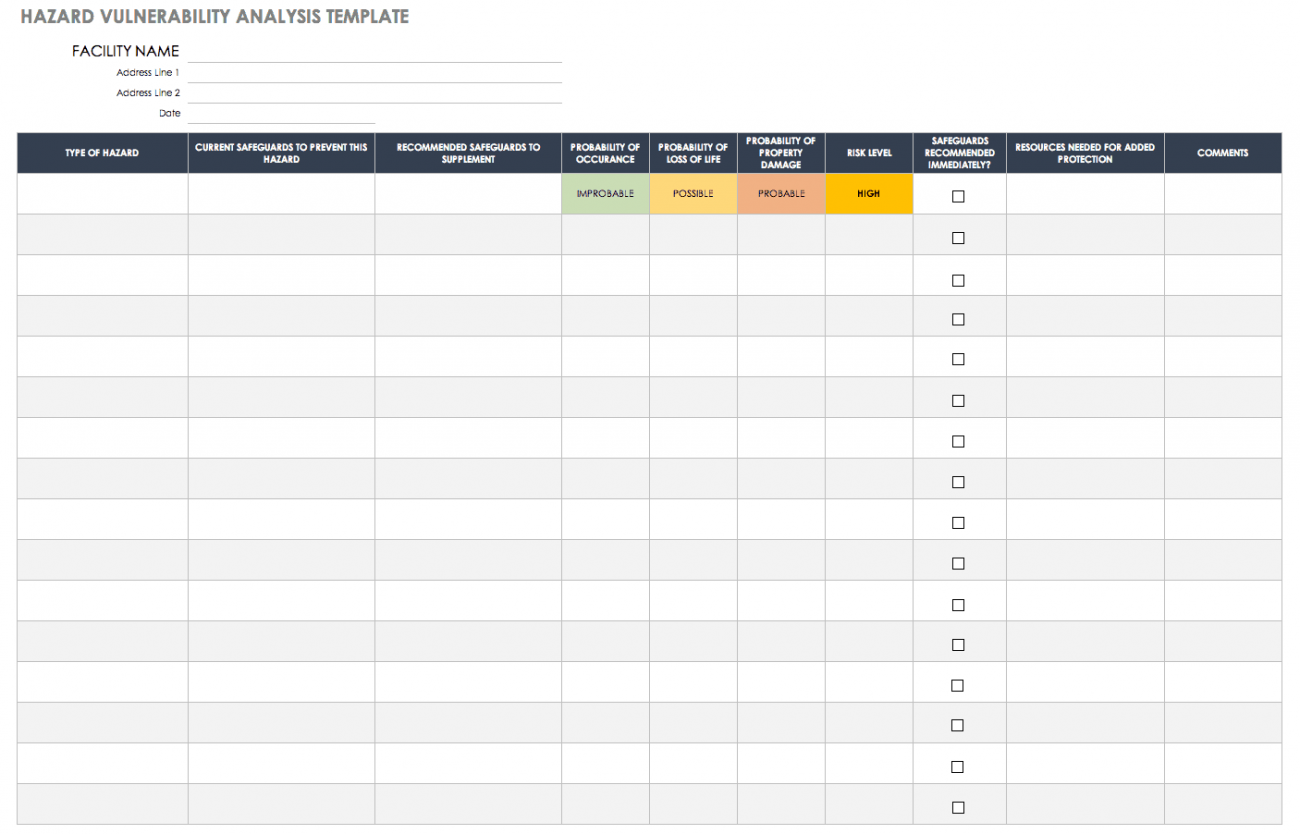
Sample Hazard Vulnerability Analysis Analysis, Vulnerability
Free Vulnerability Assessment Templates Smartsheet
Network Service Vulnerability Report SC Report Template Tenable®
Vulnerability Assessment Template Download Printable PDF Templateroller
Windows Vulnerability Summary Report SC Report Template Tenable®
The Report Is Available In The.
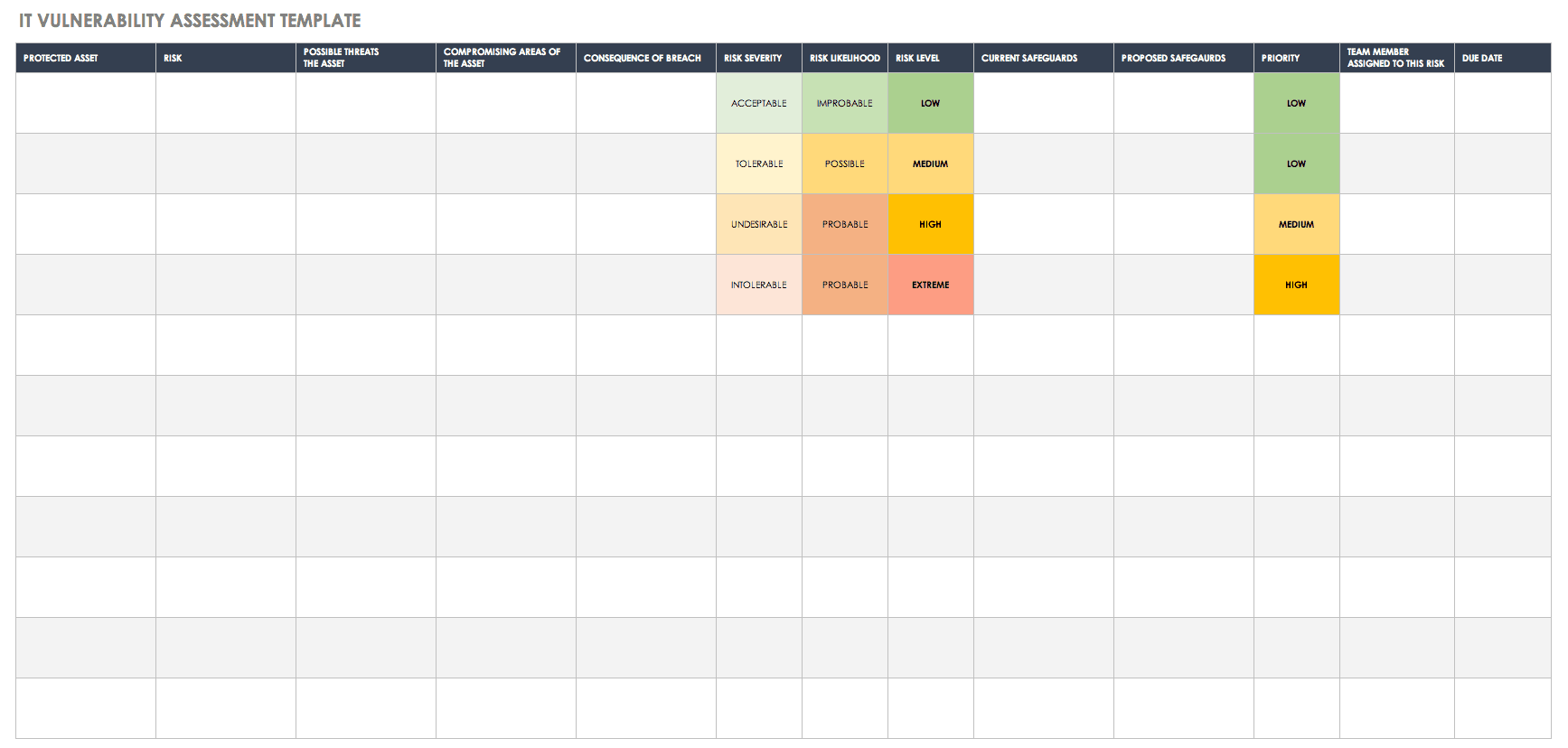
Web Typically, A Vulnerability Assessment Report Will Show You The Raw Number Of Vulnerabilities Detected In Your Systems At.
In Case You Would Like To Report A.
What Is The Problem That Creates The Vulnerability?
Related Post:


![28+ [ Vulnerability Report Template ] Vulnerability With Regard To](https://pray.gelorailmu.com/wp-content/uploads/2020/01/28-vulnerability-report-template-vulnerability-with-regard-to-threat-assessment-report-template-768x854.png)