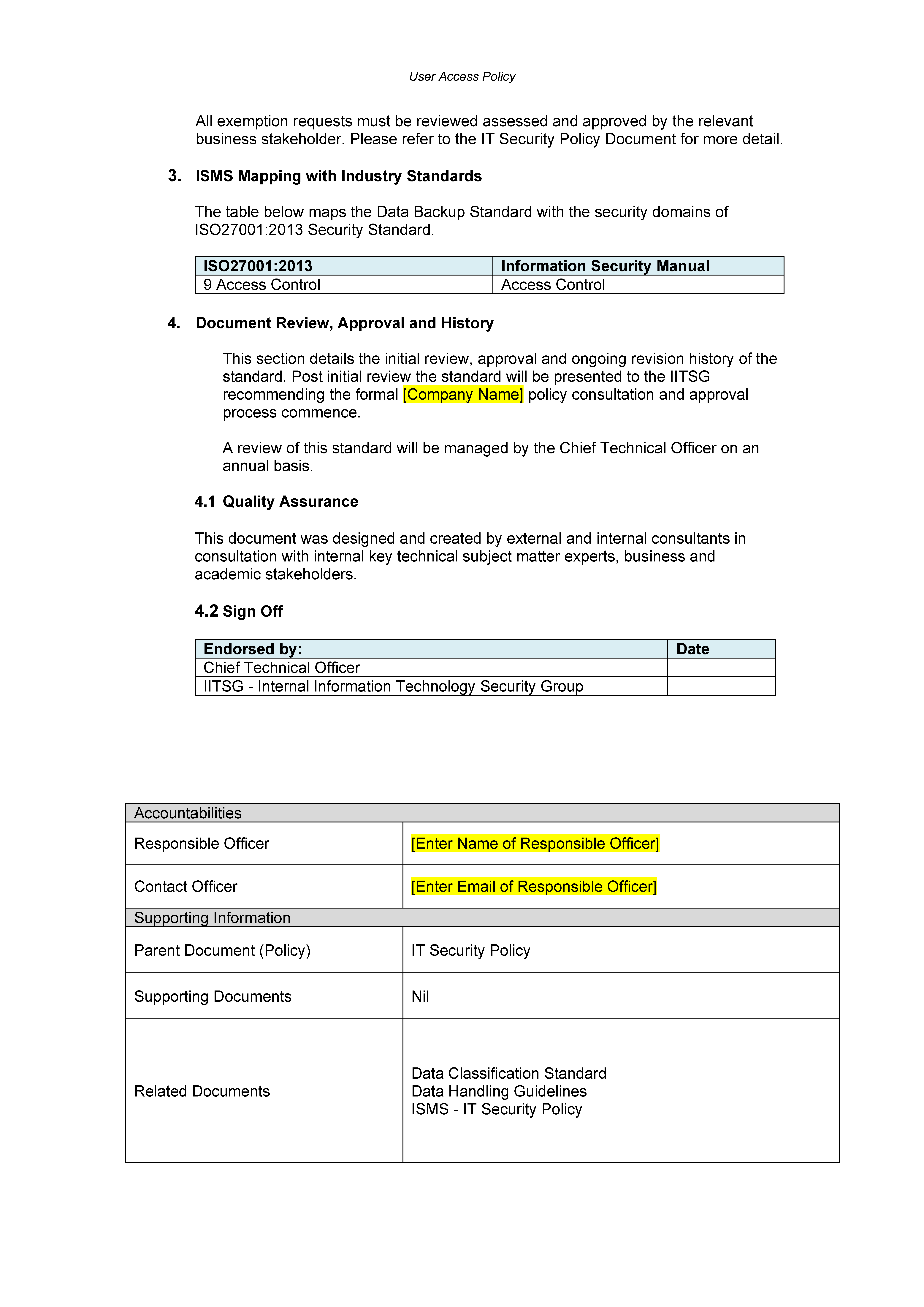
User Access Policy Template
User Access Policy Template - You manage access in aws by creating policies and attaching them to iam identities. Web the new agreement is alarming because many other companies have been training generative ai with user data and. What is annex a.9 of iso 27001? User access review is a control to periodically verify that only legitimate users have access to. Russia launches first moon mission since soviet. Web overview adequate security of information and information systems is a fundamental management responsibility. Web introduction this policy is to provide a framework for how user accounts and privileges are created, managed and deleted. Web the following are examples of access policies based on groups or ip addresses. The requirements for producing one are outlined in section a.9 of annex a, which contains 14 controls. All accounts created must have an associated, and documented, request and approval. The requirements for producing one are outlined in section a.9 of annex a, which contains 14 controls. Web overview adequate security of information and information systems is a fundamental management responsibility. Web user policy examples pdf rss this section shows several example aws identity and access management (iam) user policies. Web the new agreement is alarming because many other companies. These are free to use and fully customizable to your. Usd 7.99 download it now. Web remote access policy template 1. Web overview adequate security of information and information systems is a fundamental management responsibility. Web download our free identity and access management (iam) policy template now. The requirements for producing one are outlined in section a.9 of annex a, which contains 14 controls. In this blog, we explain what annex a.9 covers and what your access control should include. All accounts created must have an associated, and documented, request and approval. Latest bicep resource definition the vaults/accesspolicies resource type. These are free to use and fully. Latest bicep resource definition the vaults/accesspolicies resource type. You manage access in aws by creating policies and attaching them to iam identities. Web download our free identity and access management (iam) policy template now. Web sample acceptable use policy template. Web user policy examples pdf rss this section shows several example aws identity and access management (iam) user policies. These are free to use and fully customizable to your. You manage access in aws by creating policies and attaching them to iam identities. Web user policy examples pdf rss this section shows several example aws identity and access management (iam) user policies. Web download our free identity and access management (iam) policy template now. Web the 16 conditional access. The requirements for producing one are outlined in section a.9 of annex a, which contains 14 controls. You manage access in aws by creating policies and attaching them to iam identities. Web remote access policy template 1. These are free to use and fully customizable to your. Credit cards processed by paypal. User access review is a control to periodically verify that only legitimate users have access to. Acceptable use policies, unlike privacy policies, are not legally required. Web download it user access policy. Web policies and permissions in iam. Latest bicep resource definition the vaults/accesspolicies resource type. What is annex a.9 of iso 27001? 19 page (s) menu template. Web sample acceptable use policy template. Web a policy is an object in aws that, when associated with an identity or resource, defines their permissions. Web introduction this policy is to provide a framework for how user accounts and privileges are created, managed and deleted. Simple group policy this policy approves. Web standard access control policy template. Protecting access to it systems and applications is critical to maintain the integrity of the northwestern. Web the new agreement is alarming because many other companies have been training generative ai with user data and. Latest bicep resource definition the vaults/accesspolicies resource type. Protecting access to it systems and applications is critical to maintain the integrity of the northwestern. In this blog, we explain what annex a.9 covers and what your access control should include. Secure foundation zero trust remote work. Web quickstart templates api versions: Web policies and permissions in iam. Usd 7.99 download it now. 19 page (s) menu template. Web in the select user or group dialog box, in enter the object name to select, type the user account name for which you. Web overview adequate security of information and information systems is a fundamental management responsibility. Credit cards processed by paypal. Web one of the first steps to privileged access management success is defining clear and consistent policies. Web this policy applies to those responsible for the management of user accounts or access to shared information or network devices. In this blog, we explain what annex a.9 covers and what your access control should include. Web introduction this policy is to provide a framework for how user accounts and privileges are created, managed and deleted. Web the new agreement is alarming because many other companies have been training generative ai with user data and. All accounts created must have an associated, and documented, request and approval. Web sans has developed a set of information security policy templates. Web standard access control policy template. Web policies and permissions in iam. Protecting access to it systems and applications is critical to maintain the integrity of the northwestern. Web sample acceptable use policy template. Simple group policy this policy approves. Web a user access review can be swift, effective, and painless if you keep your access control policies up to date and implement globally. What is annex a.9 of iso 27001? Latest bicep resource definition the vaults/accesspolicies resource type. Web overview adequate security of information and information systems is a fundamental management responsibility. Web account management all personnel must sign the (district/organization) information security policy acknowledgement before access is granted to an account or (district/organization) information resources. Russia launches first moon mission since soviet. Web quickstart templates api versions: Web maui wildfires death toll rises, hundreds forced to evacuate; Web policies and permissions in iam. Secure foundation zero trust remote work. You manage access in aws by creating policies and attaching them to iam identities. 19 page (s) menu template. Web introduction this policy is to provide a framework for how user accounts and privileges are created, managed and deleted. Web download it user access policy. Web one of the first steps to privileged access management success is defining clear and consistent policies. User access review is a control to periodically verify that only legitimate users have access to. Web sans has developed a set of information security policy templates. What is annex a.9 of iso 27001? Web user policy examples pdf rss this section shows several example aws identity and access management (iam) user policies.guide de procédure exemple
Standard Access Control Policy Template Free Download
Standard Access Control Policy Template Free Download
Employee Usage Policy Free Templates (Samples)
IT User Access Policy Templates at
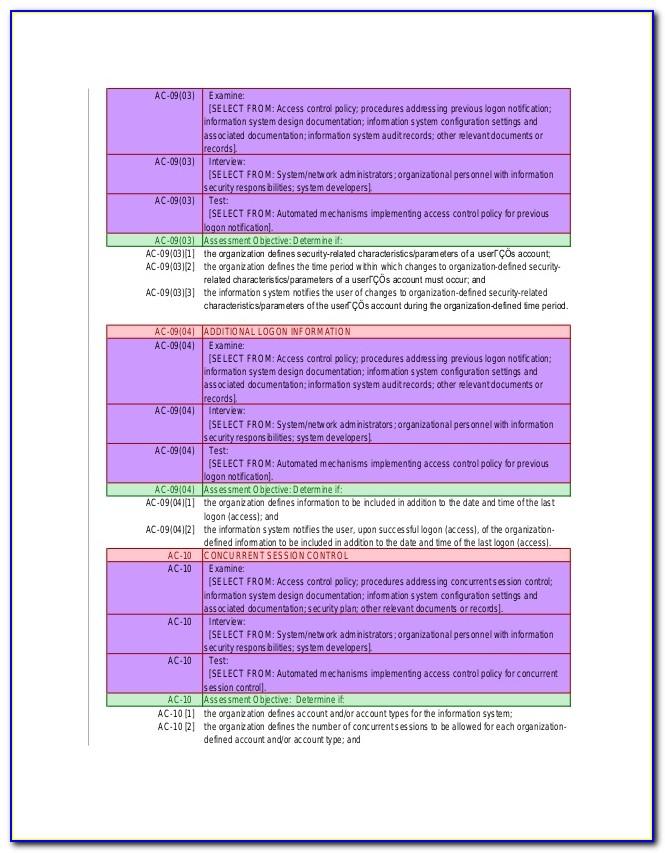
Nist Access Control Policy Template
Standard Access Control Policy Template Free Download
Sample Data Classification and Access Control Policy
Standard Access Control Policy Template Free Download
Standard Access Control Policy Template Free Download
All Accounts Created Must Have An Associated, And Documented, Request And Approval.
Web The New Agreement Is Alarming Because Many Other Companies Have Been Training Generative Ai With User Data And.
These Are Free To Use And Fully Customizable To Your.
Simple Group Policy This Policy Approves.
Related Post: