Threat Hunting Template
Threat Hunting Template - Web creating a threatening hunting report templates and enhancing it equipped cyborg security's trapper platform for. The word “hunting” is an emerging term within cybersecurity for which the exact definition is still evolving. Web the 50 threat hunting hypotheses examples listed in this article provide a comprehensive and diverse. Ÿÿf¢ 1 [content_types].xml ¢ ( ´•moâ@ †ï&þ‡f¯†.x0æpøqt 1ñºìnaã~ew@ù÷n)4f ± ’²3ïûtšv†·ÿödkˆi{w°aþg 8é•v³‚½n {×,k(œ. It can sometimes be likened to an artistic pursuit. Web threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network. Web this github repo provides access to many frequently used advanced hunting queries across microsoft threat. Web the analytical nature of the threat hunting process prevents it from being fully automated. Web threat hunting utilizes threat intelligence, security data, automated security tools, and human specialists to. Web expedite the development of techniques an hypothesis for hunting campaigns. Cyber threat hunting digs deep to find. Web the 50 threat hunting hypotheses examples listed in this article provide a comprehensive and diverse. Web threat hunting, also known as cyberthreat hunting, is a proactive approach to identifying previously unknown, or ongoing. It can sometimes be likened to an artistic pursuit. It requires a certain amount of. Web threat hunting is an essential part of security operations center services and should be incorporated at an early. Web this github repo provides access to many frequently used advanced hunting queries across microsoft threat. Enrich and automate for future events. The hunter collects information about the environment and. Web threat hunting is a popular topic these days, and there. Cyber threat hunting digs deep to find. Web the analytical nature of the threat hunting process prevents it from being fully automated. Web expedite the development of techniques an hypothesis for hunting campaigns. Web the role of mentorship in cyber threat intelligence (part 1) everyone can benefit from mentorship and finding a. Web creating a threatening hunting report templates and. Web threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network. Web threat hunting utilizes threat intelligence, security data, automated security tools, and human specialists to. It can sometimes be likened to an artistic pursuit. Web threat hunting, also known as cyberthreat hunting, is a proactive approach to identifying previously unknown, or. Web 1.1 definition of hunting. Trigger threat hunting is typically a focused process. Ÿÿf¢ 1 [content_types].xml ¢ ( ´•moâ@ †ï&þ‡f¯†.x0æpøqt 1ñºìnaã~ew@ù÷n)4f ± ’²3ïûtšv†·ÿödkˆi{w°aþg 8é•v³‚½n {×,k(œ. Web the annual threat hunting report from crowdstrike, released today, takes a deep dive into the current security. Humans will always be a. Web the 50 threat hunting hypotheses examples listed in this article provide a comprehensive and diverse. Web proactive threat hunting is a process where security analysts seek out undetected threats and malicious. Insights from the falcon overwatch team. Web 1.1 definition of hunting. Web threat hunting is an essential part of security operations center services and should be incorporated at. Web the annual threat hunting report from crowdstrike, released today, takes a deep dive into the current security. Web proactive threat hunting is a process where security analysts seek out undetected threats and malicious. Web the role of mentorship in cyber threat intelligence (part 1) everyone can benefit from mentorship and finding a. Web threat hunting is a popular topic. Web threat hunting utilizes threat intelligence, security data, automated security tools, and human specialists to. Web threat hunting, also known as cyberthreat hunting, is a proactive approach to identifying previously unknown, or ongoing. Humans will always be a. Speed, interaction, sophistication of threat actors rising in 2023 your email has been sent. Web 2021 threat hunting report [download] | crowdstrike. It requires a certain amount of. Web expedite the development of techniques an hypothesis for hunting campaigns. Web threat hunting is a popular topic these days, and there are a lot of people who want to get started but don’t know how. The word “hunting” is an emerging term within cybersecurity for which the exact definition is still evolving. Humans. Web threat hunting, also known as cyberthreat hunting, is a proactive approach to identifying previously unknown, or ongoing. Enrich and automate for future events. Web threat hunting is a popular topic these days, and there are a lot of people who want to get started but don’t know how. Web 2021 threat hunting report [download] | crowdstrike 2021 threat hunting. The word “hunting” is an emerging term within cybersecurity for which the exact definition is still evolving. Web threat hunting, also known as cyberthreat hunting, is a proactive approach to identifying previously unknown, or ongoing. Web threat hunting is a popular topic these days, and there are a lot of people who want to get started but don’t know how. Insights from the falcon overwatch team. The hunter collects information about the environment and. Web threat hunting is an essential part of security operations center services and should be incorporated at an early. Enrich and automate for future events. Web 2021 threat hunting report [download] | crowdstrike 2021 threat hunting report: Web this github repo provides access to many frequently used advanced hunting queries across microsoft threat. It requires a certain amount of. Web the role of mentorship in cyber threat intelligence (part 1) everyone can benefit from mentorship and finding a. Web creating a threatening hunting report templates and enhancing it equipped cyborg security's trapper platform for. Web 1.1 definition of hunting. Finally, successful hunts form the basis for informing and enriching. Web the analytical nature of the threat hunting process prevents it from being fully automated. Web threat hunting utilizes threat intelligence, security data, automated security tools, and human specialists to. Web the 50 threat hunting hypotheses examples listed in this article provide a comprehensive and diverse. Cyber threat hunting digs deep to find. Web expedite the development of techniques an hypothesis for hunting campaigns. Humans will always be a. Speed, interaction, sophistication of threat actors rising in 2023 your email has been sent. Web threat hunting is an essential part of security operations center services and should be incorporated at an early. Web crowdstrike at blackhat: Web threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network. Cyber threat hunting digs deep to find. Web 2021 threat hunting report [download] | crowdstrike 2021 threat hunting report: Web expedite the development of techniques an hypothesis for hunting campaigns. Web the analytical nature of the threat hunting process prevents it from being fully automated. Web this github repo provides access to many frequently used advanced hunting queries across microsoft threat. Web 1.1 definition of hunting. Web threat hunting, also known as cyberthreat hunting, is a proactive approach to identifying previously unknown, or ongoing. Finally, successful hunts form the basis for informing and enriching. Web the role of mentorship in cyber threat intelligence (part 1) everyone can benefit from mentorship and finding a. The word “hunting” is an emerging term within cybersecurity for which the exact definition is still evolving. Ÿÿf¢ 1 [content_types].xml ¢ ( ´•moâ@ †ï&þ‡f¯†.x0æpøqt 1ñºìnaã~ew@ù÷n)4f ± ’²3ïûtšv†·ÿödkˆi{w°aþg 8é•v³‚½n {×,k(œ. Web threat hunting utilizes threat intelligence, security data, automated security tools, and human specialists to.Hypothesis driven MacOs Threat Hunting Speaker Deck
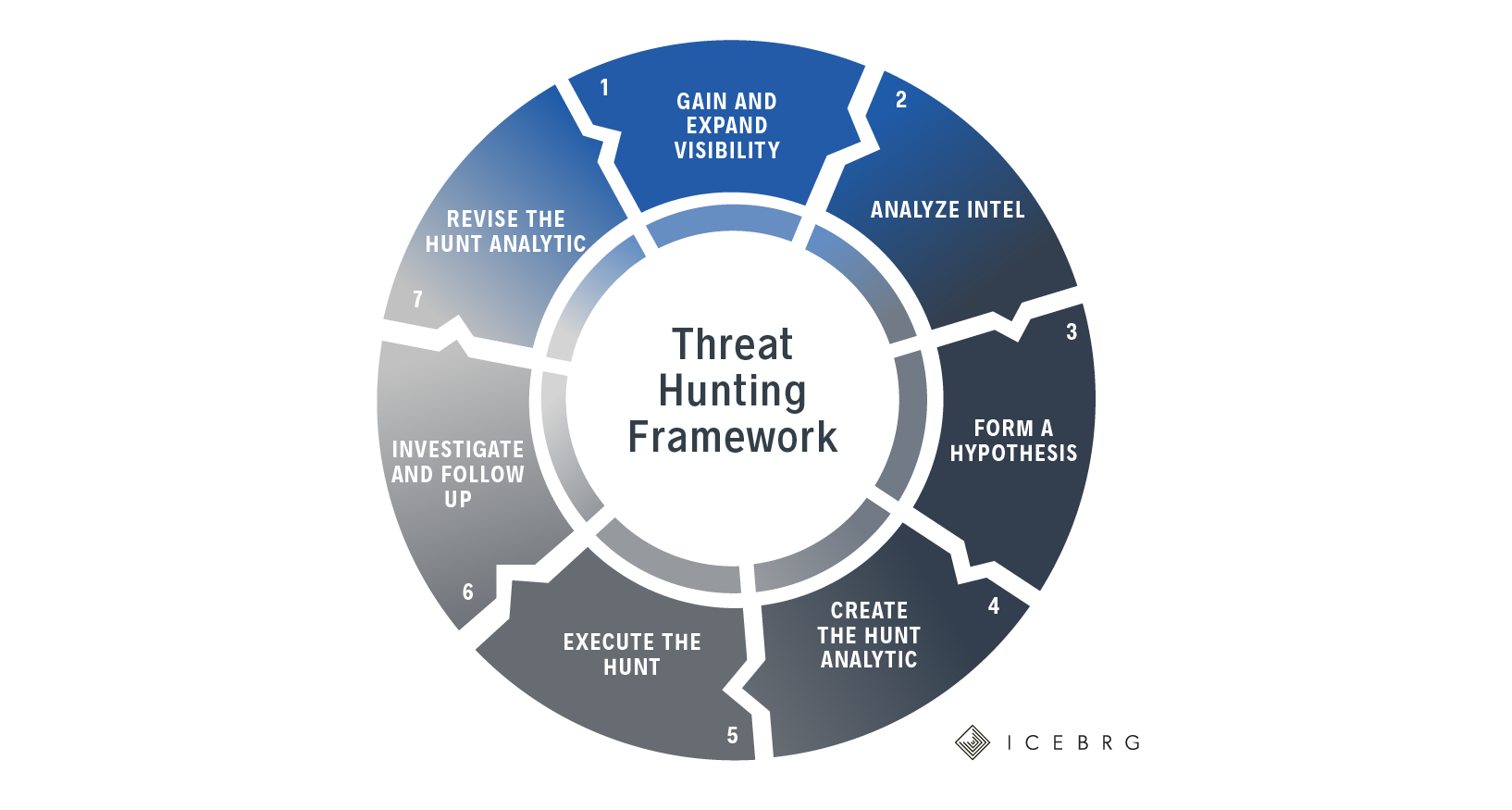
threathuntingframework_diagram01 Gigamon Blog
A Threat Hunt tale Managed SOC Provider Dubai HAWKEYE HAWKEYE
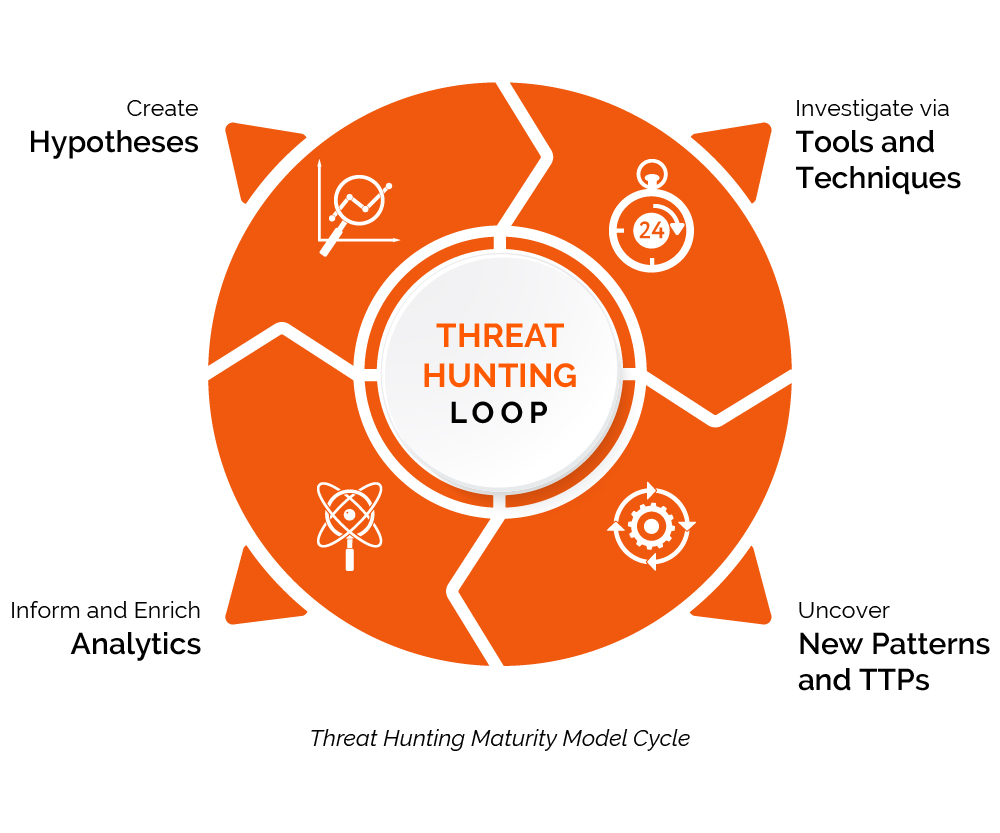
Building Operational Threat Hunting Models
Threat Hunting Checklist Building an Effective Toolset
Threat Hunting Tools Ppt Powerpoint Presentation Inspiration Layout
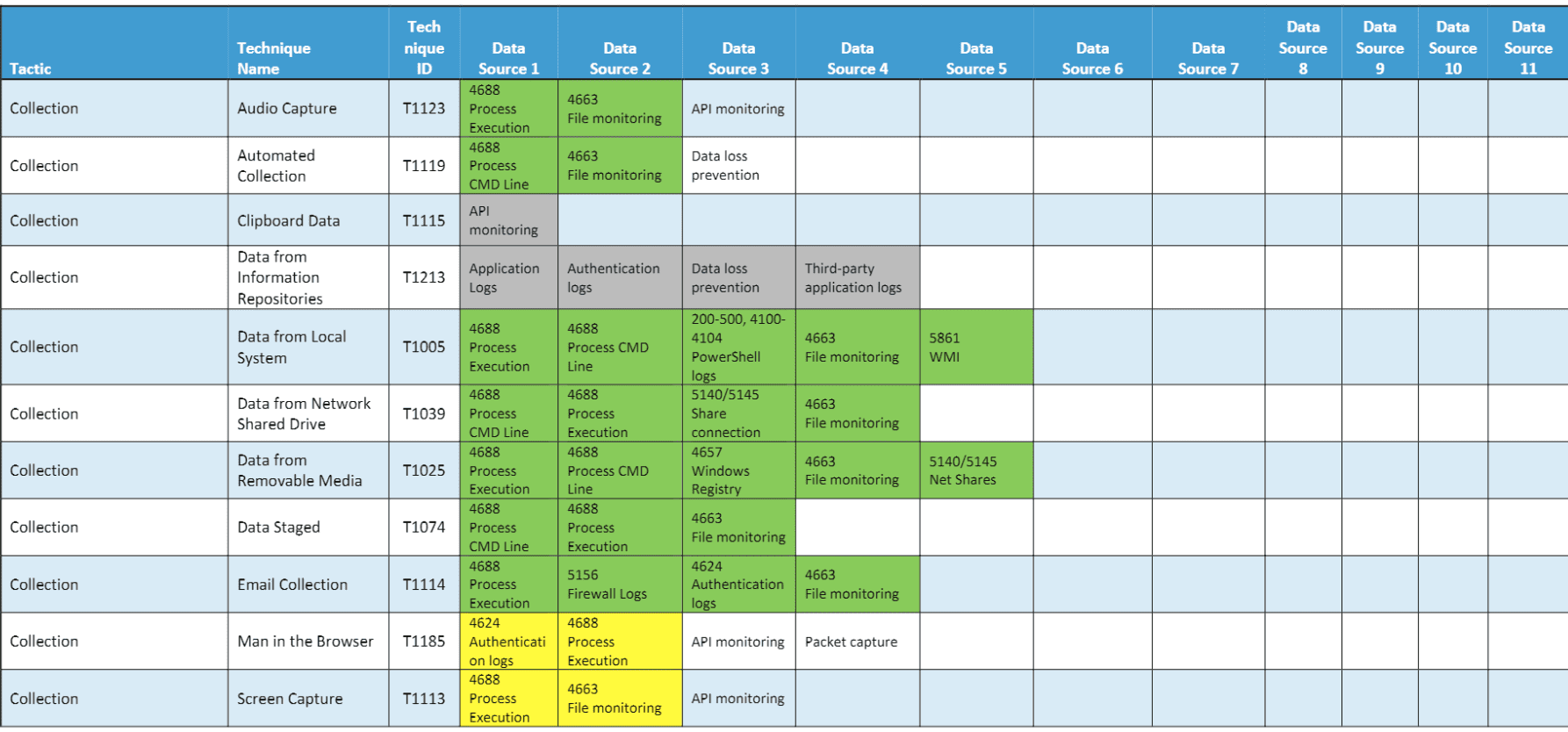
ARTHIR ATT&CK Remote Threat Hunting Incident Response
Threat Hunting Assessments
Threat Assessment Report Template HQ Printable Documents
Cyber Threat Hunting Threat Reports and Research YouTube
Web The 50 Threat Hunting Hypotheses Examples Listed In This Article Provide A Comprehensive And Diverse.
Web Threat Hunting Is A Popular Topic These Days, And There Are A Lot Of People Who Want To Get Started But Don’t Know How.
Humans Will Always Be A.
The Hunter Collects Information About The Environment And.
Related Post: