Information Security Template
Information Security Template - Web sans has developed a set of information security policy templates. It needs to be robust and secure your organization from all ends. Security policies come in several forms, including the following: Just download pptx and open the. Determine what phi you have access to. Web best information security powerpoint templates. Web the policy templates are provided courtesy of the state of new york and the state of california. Web cloud controls matrix template (june 2023)202kb.xlsx the australian cyber security centre (acsc) produces the. Web policies are foundational components of security programs. Web this template also includes a question reference column where you might, for example, list an iso 27001 step. Web this presentation template 2673 is complete compatible with google slides. Designed to save hours of work and prewritten and fully populated the iso 27001 information security. Web 42 information security policy templates [cyber security] a security policy can either be a single document or a set of documents related to. Web information security, often referred to as infosec, refers. Web this iso 27001 risk assessment template provides everything you need to determine any vulnerabilities in your information security. Web best information security powerpoint templates. Web an information security policy can be tough to build from scratch; Security policies come in several forms, including the following: Web this template also includes a question reference column where you might, for example,. Web policies are foundational components of security programs. Web this information security risk assessment template includes a column for iso 27001, so you can apply any of the international. Web the policy templates are provided courtesy of the state of new york and the state of california. Manchester memorial hospital is seen friday, aug. Web 3 of 5 |. Web information security is a broader category of protections, covering cryptography, mobile computing, and social media. These are free to use and fully customizable to your. Determine what phi you have access to. Abbreviations / acronyms / synonyms: Web in this article, we will discuss the information security policy template. Share to facebook share to twitter. Web the employee benefits security administration of the u.s. Web the policy templates are provided courtesy of the state of new york and the state of california. Web 42 information security policy templates [cyber security] a security policy can either be a single document or a set of documents related to. Web 3 of. Web examples of security policies. Web the policy templates are provided courtesy of the state of new york and the state of california. Designed to save hours of work and prewritten and fully populated the iso 27001 information security. These are free to use and fully customizable to your. A security incident is an event that is reported by the. These are free to use and fully customizable to your. Department of labor (the department) is. Web information security policy template. Web this template also includes a question reference column where you might, for example, list an iso 27001 step. Guide how infosec decisions are made with our information security policy template. Guide how infosec decisions are made with our information security policy template. Digital presentations are a modern way of conveying information that. Web examples of security policies. Web we’ve already published new templates as curated collections of settings for specific scenarios and baselines which. Identify where your organization is vulnerable. Web 42 information security policy templates [cyber security] a security policy can either be a single document or a set of documents related to. Digital presentations are a modern way of conveying information that. Web we’ve already published new templates as curated collections of settings for specific scenarios and baselines which. Web policies are foundational components of security programs. Web. Determine what phi you have access to. Web below you will find a template that will help you plan for data security and guide you in the development of other. Web information security is a broader category of protections, covering cryptography, mobile computing, and social media. Digital presentations are a modern way of conveying information that. Web policies are foundational. Web in this article, we will discuss the information security policy template. Security policies come in several forms, including the following: Web the policy templates are provided courtesy of the state of new york and the state of california. Web information security is a broader category of protections, covering cryptography, mobile computing, and social media. Web we’ve already published new templates as curated collections of settings for specific scenarios and baselines which. A security incident is an event that is reported by the security. Abbreviations / acronyms / synonyms: The information security policy template that has been provided requires some areas to. Web below you will find a template that will help you plan for data security and guide you in the development of other. Web examples of security policies. Web this template also includes a question reference column where you might, for example, list an iso 27001 step. Web this presentation template 2673 is complete compatible with google slides. Web policies are foundational components of security programs. Share to facebook share to twitter. Web 3 of 5 |. Just download pptx and open the. Identify where your organization is vulnerable. Web our iso 27001 information security policy template gives you a head start on your documentation process. 4, 2023 in manchester, conn. Web 42 information security policy templates [cyber security] a security policy can either be a single document or a set of documents related to. Guide how infosec decisions are made with our information security policy template. Web security incident report form. Share to facebook share to twitter. Web in this article, we will discuss the information security policy template. Department of labor (the department) is. Web this iso 27001 risk assessment template provides everything you need to determine any vulnerabilities in your information security. Identify where your organization is vulnerable. Just download pptx and open the. Web cloud controls matrix template (june 2023)202kb.xlsx the australian cyber security centre (acsc) produces the. Abbreviations / acronyms / synonyms: Web best information security powerpoint templates. Digital presentations are a modern way of conveying information that. Web creating and implementing an information security policy is a vital component of any company’s cyber security strategy, and is. It needs to be robust and secure your organization from all ends. Determine what phi you have access to. Web policies are foundational components of security programs.Information Security Policy Template for Recruitment Agencies & Offices
Cyber Security PowerPoint Template and Keynote Slide Slidebazaar
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
Information Security Plan Template Information Security Today
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
Addictionary
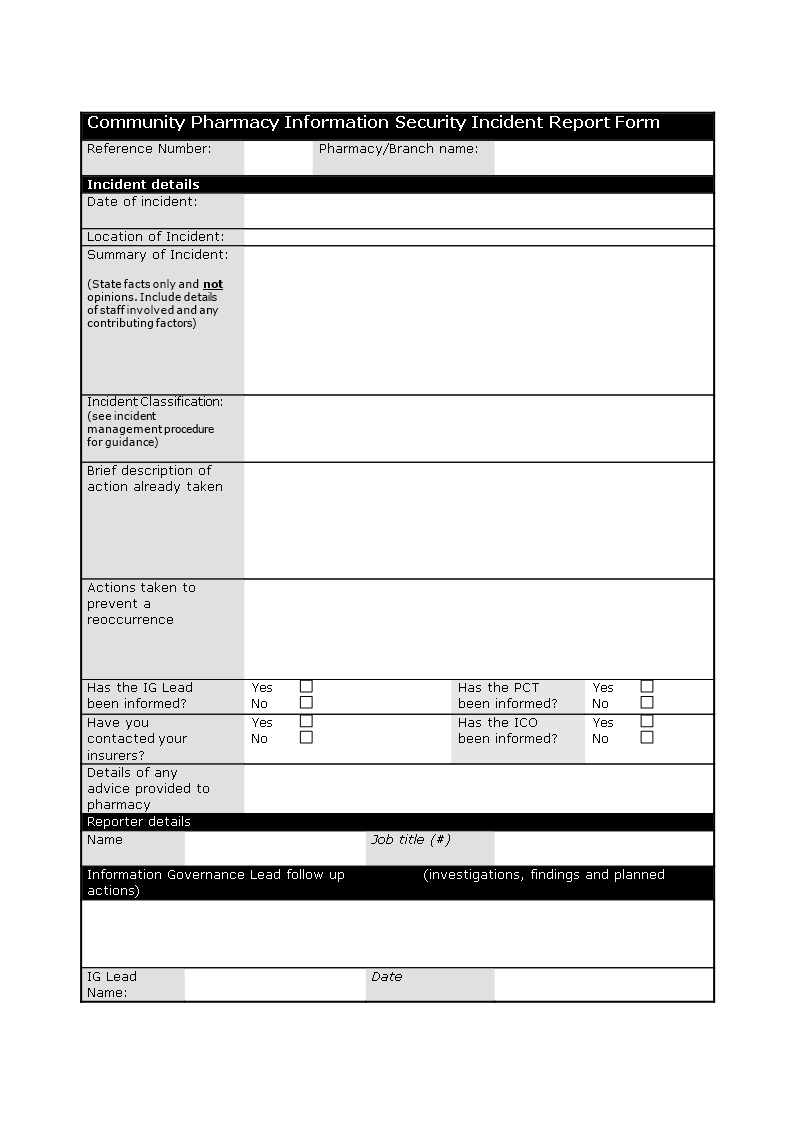
免费 Information Security Incident Report template 样本文件在
Web This Presentation Template 2673 Is Complete Compatible With Google Slides.
Web The Employee Benefits Security Administration Of The U.s.
Web Iso 27001 Information Security Policy Template.
The Information Security Policy Template That Has Been Provided Requires Some Areas To.
Related Post:


![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-32.jpg?w=395)
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-02.jpg)
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-10.jpg)

![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-03.jpg?w=395)
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-13.jpg)