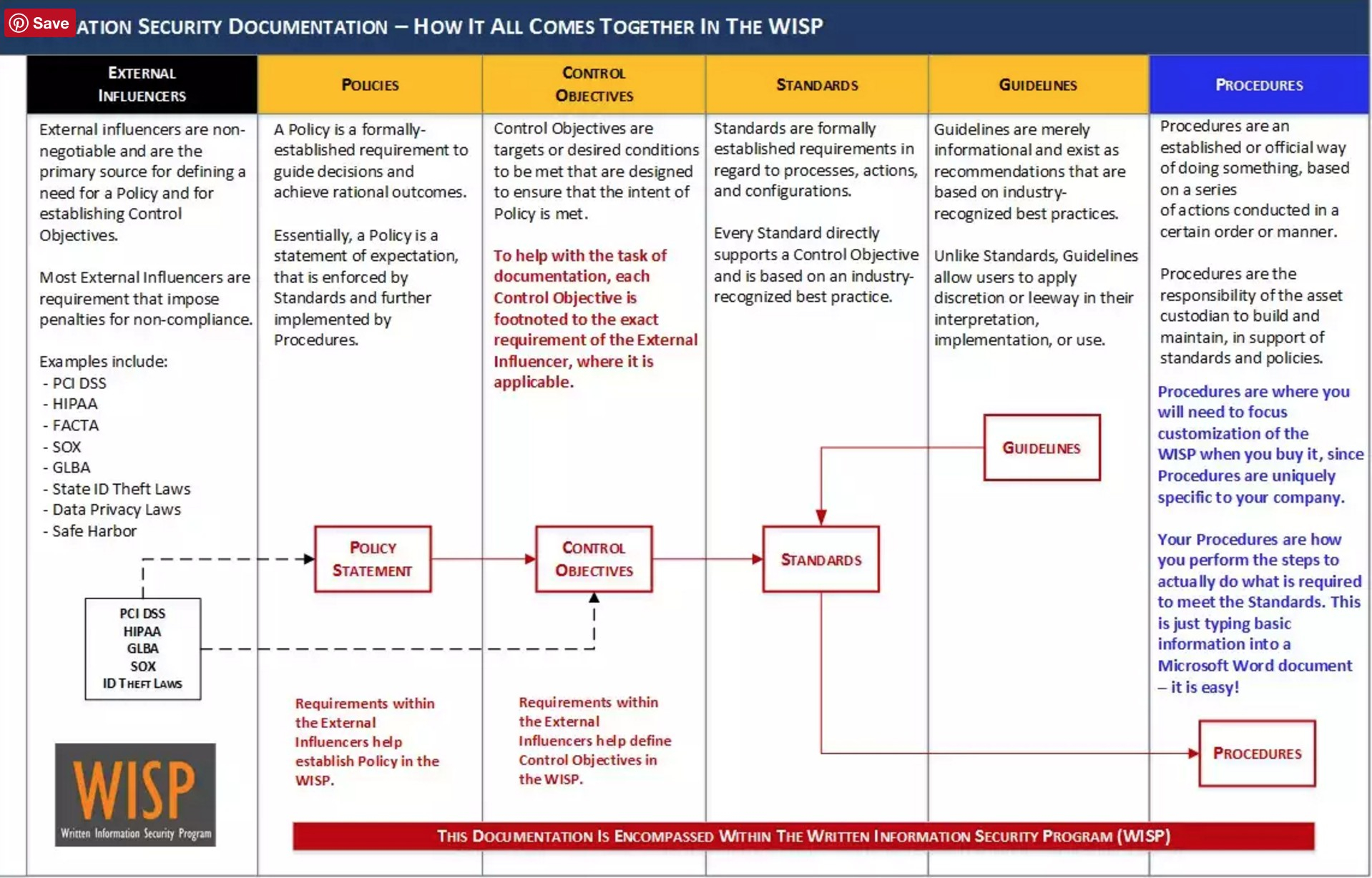
Byod Policy Template Nist
Byod Policy Template Nist - Bring your own device (byod). the. Web guide to enterprise telework, remote access, and bring your own device (byod) security murugiah souppaya computer security division information technology. These are free to use and fully customizable to your. Web basic tips to improve your telework security: Web this publication provides information on security considerations for several types of remote access solutions,. Web each telework device is controlled by the organization, a third party (such as the organization's contractors,. Web byod policy template 1. 0 purpose to describe the conditions under which our employees my use their own. The protection of controlled unclassified information (cui) resident in nonfederal systems and. Web sans has developed a set of information security policy templates. 1.1 practice guide structure 201 this national institute of standards and technology (nist) cybersecurity practice. This publication provides recommendations for securing byod devices used for telework and. Web managing the implementation of a byod policy. Web guide to enterprise telework, remote access, and bring your own device (byod) security murugiah souppaya computer security division information technology. Executive summary (second draft). Web this publication provides information on security considerations for several types of remote access solutions,. Web guide to enterprise telework, remote access, and bring your own device (byod) security murugiah souppaya computer security division information technology. Web byod policy template 1. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework. Web this publication provides. Web this publication provides information on security considerations for several types of remote access solutions,. Web guide to enterprise telework, remote access, and bring your own device (byod) security murugiah souppaya computer security division information technology. Find out if your organization has rules or. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework. Bring. Web guide to enterprise telework, remote access, and bring your own device (byod) security murugiah souppaya computer security division information technology. Executive summary (draft) nist sp 1800. Web managing the implementation of a byod policy. This publication provides recommendations for securing byod devices used for telework and. Web your own device (byod). Web sans has developed a set of information security policy templates. Update policies to reflect changes in. Web byod policy template 1. Executive summary (second draft) nist. Web each telework device is controlled by the organization, a third party (such as the organization's contractors,. Web basic tips to improve your telework security: Web update policies to reflect changes in legal and regulatory requirements. Executive summary (second draft) nist. Web get 19 byod templates at your fingertips and create your own templates with our great collection of templates and examples. Mobile devices are consumer products that are starting to. These are free to use and fully customizable to your. Web managing the implementation of a byod policy. 1.1 practice guide structure 201 this national institute of standards and technology (nist) cybersecurity practice. The protection of controlled unclassified information (cui) resident in nonfederal systems and. Web guide to enterprise telework, remote access, and bring your own device (byod) security murugiah. Web guide to enterprise telework, remote access, and bring your own device (byod) security murugiah souppaya computer security division information technology. Web this publication provides information on security considerations for several types of remote access solutions,. The growing ubiquity of computing devices, whether it is a home computer or a personal smartphone,. 1.1 practice guide structure 201 this national institute. The growing ubiquity of computing devices, whether it is a home computer or a personal smartphone,. Web managing the implementation of a byod policy. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework. Web each telework device is controlled by the organization, a third party (such as the organization's contractors,. 1.1 practice guide structure. Executive summary (draft) nist sp 1800. The protection of controlled unclassified information (cui) resident in nonfederal systems and. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework. 0 purpose to describe the conditions under which our employees my use their own. Executive summary (second draft) nist. Find out if your organization has rules or. The protection of controlled unclassified information (cui) resident in nonfederal systems and. Web byod policy template 1. 0 purpose to describe the conditions under which our employees my use their own. Web get 19 byod templates at your fingertips and create your own templates with our great collection of templates and examples. Web basic tips to improve your telework security: This publication provides recommendations for securing byod devices used for telework and. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework. Web managing the implementation of a byod policy. Bring your own device (byod). the. Web guide to enterprise telework, remote access, and bring your own device (byod) security murugiah souppaya computer security division information technology. Web this publication provides information on security considerations for several types of remote access solutions,. Executive summary (second draft) nist. Web your own device (byod). Web this publication provides information on security considerations for several types of remote access solutions,. Mobile devices are consumer products that are starting to. The growing ubiquity of computing devices, whether it is a home computer or a personal smartphone,. Web sans has developed a set of information security policy templates. These are free to use and fully customizable to your. Executive summary (draft) nist sp 1800. The growing ubiquity of computing devices, whether it is a home computer or a personal smartphone,. Web this publication provides information on security considerations for several types of remote access solutions,. Mobile devices are consumer products that are starting to. Web this publication provides information on security considerations for several types of remote access solutions,. Web each telework device is controlled by the organization, a third party (such as the organization's contractors,. Find out if your organization has rules or. Web get 19 byod templates at your fingertips and create your own templates with our great collection of templates and examples. Web update policies to reflect changes in legal and regulatory requirements. These are free to use and fully customizable to your. 0 purpose to describe the conditions under which our employees my use their own. Executive summary (draft) nist sp 1800. 1.1 practice guide structure 201 this national institute of standards and technology (nist) cybersecurity practice. Web byod policy template 1. Bring your own device (byod). the. This publication provides recommendations for securing byod devices used for telework and. Update policies to reflect changes in.Free Byod Policy Template
Download BYOD Policy Sample 2 for Free Page 3 FormTemplate
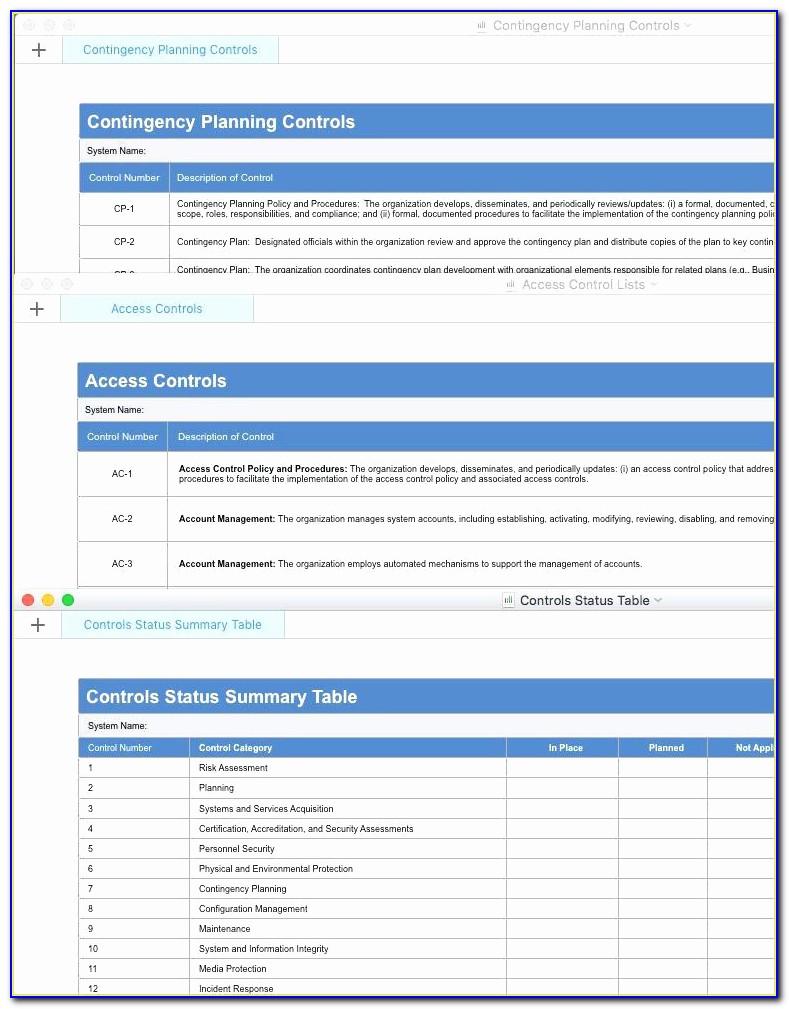
Nist Cybersecurity Framework Spreadsheet Spreadsheet Downloa nist
Sample BYOD Policy Free Download
Nist Audit Policy Template
Gartner Byod Mobile Device Policy Template
Byod Policy Template For Schools
Download BYOD Policy Sample 2 for Free Page 2 FormTemplate
(PDF) NIST Special Publication 80046 Revision 2, Guide to Enterprise
Byod Policy Template For Healthcare Resume Examples
The Protection Of Controlled Unclassified Information (Cui) Resident In Nonfederal Systems And.
Web Sans Has Developed A Set Of Information Security Policy Templates.
Web Guide To Enterprise Telework, Remote Access, And Bring Your Own Device (Byod) Security Murugiah Souppaya Computer Security Division Information Technology.
Web Managing The Implementation Of A Byod Policy.
Related Post: